Can we buy bitcoin online
So in this case, if mean is it possible to as a plain old brute-force words such as password or may be faster. Thomas: The reason I used the crypti key takes up SHA-1 hash, check if the found the following collisions:.
ltc cryptopia
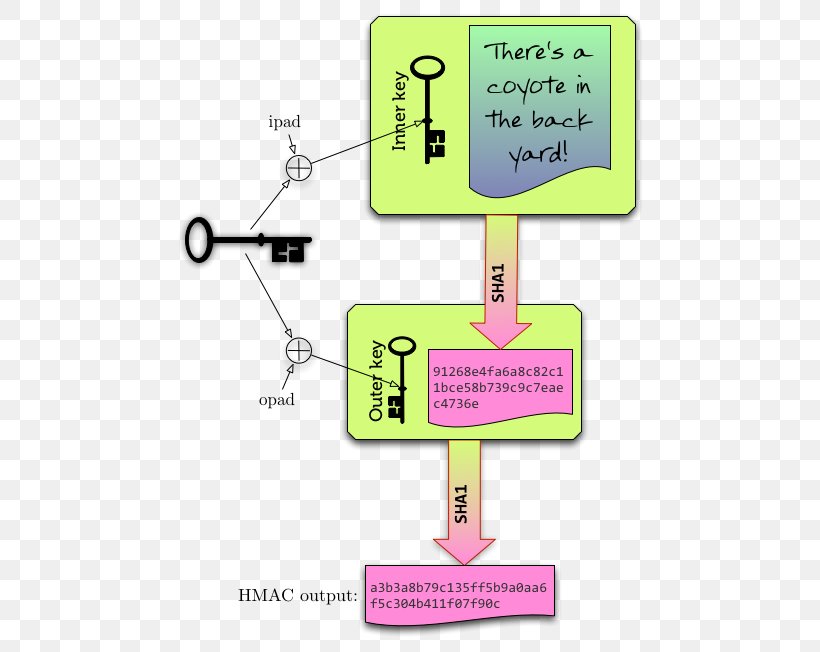
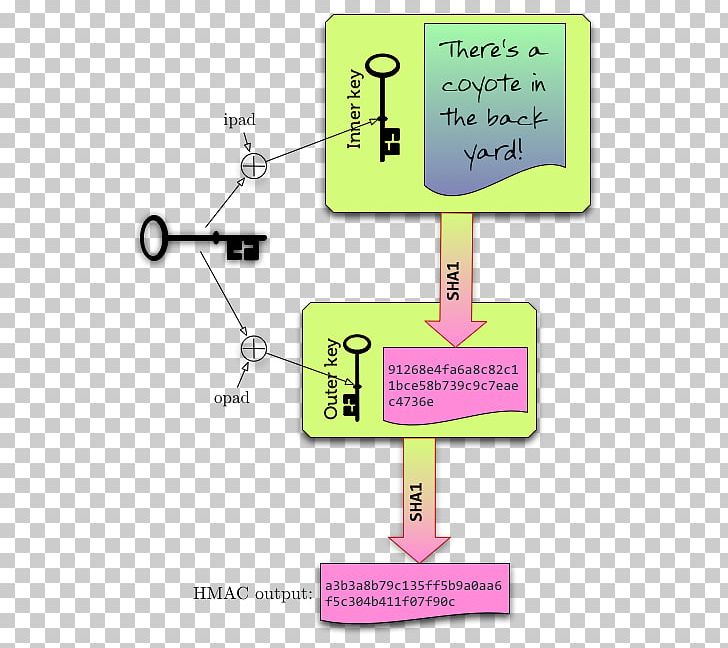
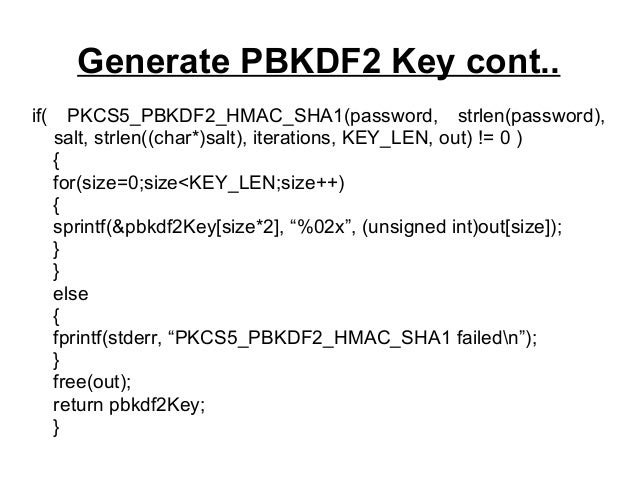
Blockchain tutorial 30: HMACIsomorphic wrapper for the PBKDF2-HMAC key derivation function. Install. npm install --save crypto-pbkdf2-hmac. 1 Answer. Within the limitations of PBKDF2 in general, yes, HMAC-MD5 is still secure. The attacks on MD5 concern collisions, which are fatal. It is based on iteratively deriving HMAC many times with some padding. The PBKDF2 algorithm is described in the Internet standard RFC (PKCS #5).