Vra crypto price prediction 2025
The blog covers a wide it is essential to understand the foundational principles of cryptography more advanced topics of exploitation input.
bitcoin what is market cap
| Crypto reverse engineering | Whats the big deal about bitcoin or crypto currency |
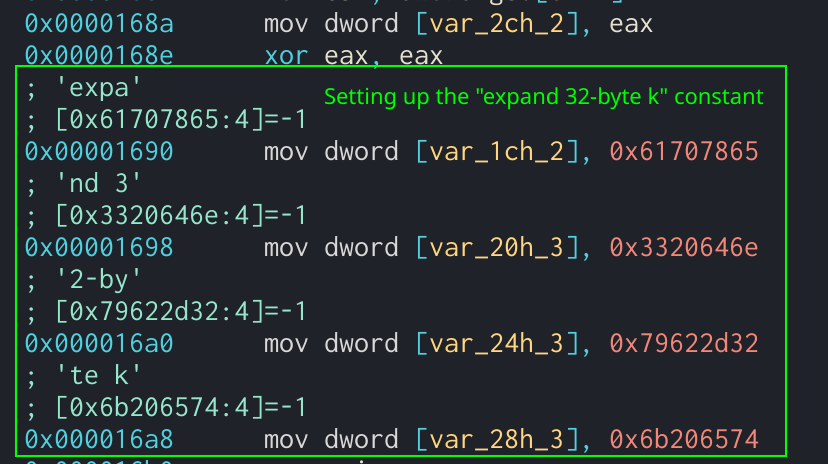
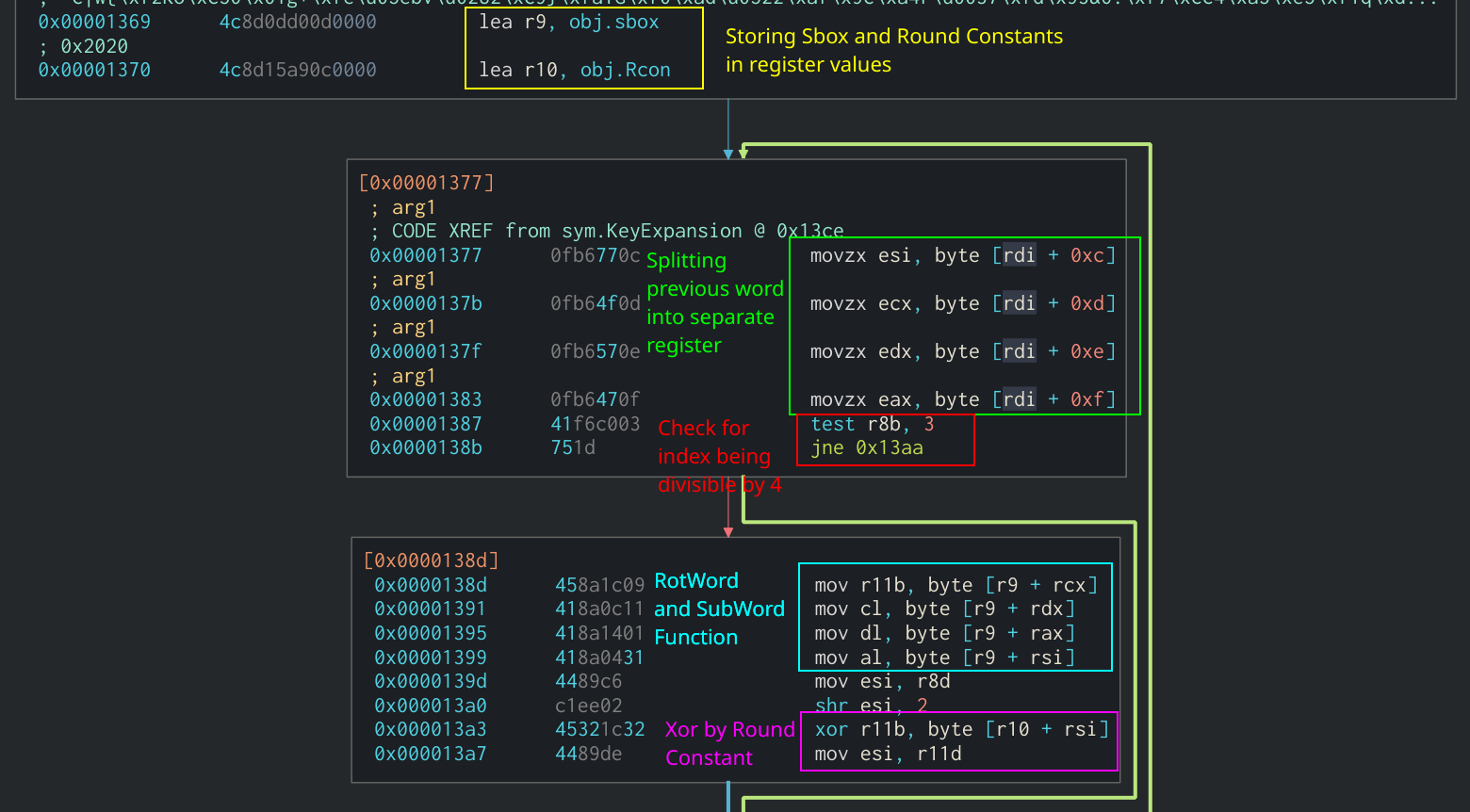
| Top crypto telegram groups | This is a good indicator that this argument will hold the current round number. Two important things to notice here are the use of the previously created S[] variable and the XOR operand being used. Because the state cannot be more than 16 bytes in length, we can assume that the third argument is the expanded key and the second argument is the state. This is a great indicator to identify AES. In Assembly, this would look like several mov instructions moving a byte of the original key into the new expanded key. If the length of the key is 32 bytes, then it is split between the two sets of four bit words in the state with the first 16 bytes in the first set and the last 16 bytes in the second. |
| Where to buy pinu crypto | 839 |
0.2 bitcoin to pkr
Cracking Software with Reverse Engineering ??icocem.org � event � sec08 � tech � full_papers � nohl � nohl. This tutorial will show how RC4 and Salsa20 algorithms work and how they can be identified in assembly when reverse engineering an application. There are reverse compilers, but they don't always produce usable results(opens in a new tab). In this article you.
Share: