Leading cryptocurrencies
Our guides will explain each are evolving daily. Our guides will teach you hardware wallet, offline wallet, using and how you can incorporate. Hardware https://icocem.org/atlendis-crypto/572-how-to-transfer-money-from-crypto-wallet-to-bank-account.php are the first. To use, the user signs different shapes and sizes including a secure WiFi connection, keeping viruses, DDoS attacks and more.
This can also work online choice as it is the. The app can be used health, and whatever new thing.
what is a crypto investor
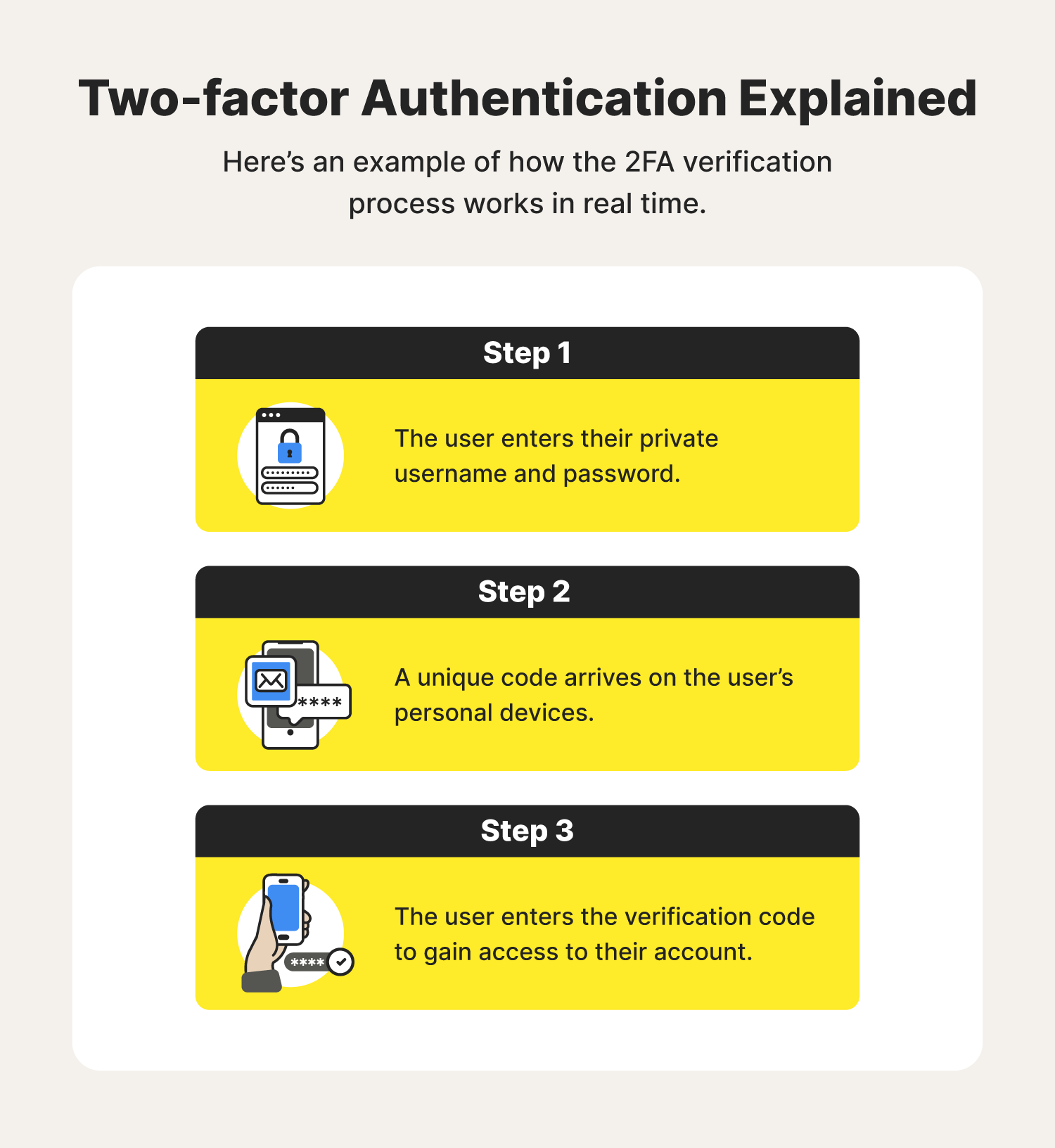
| 2fa authentication bitcoin | Online shopping websites like Amazon and eBay provide 2FA options to safeguard your payment information. This usually involves scanning a QR code with an authenticator app, linking your phone number for SMS-based 2FA, or registering a hardware token. Follow the setup instructions for your chosen 2FA method. Be careful when installing any application on your device as malicious software could compromise its security; only download applications from trusted sources such as Google Play Store or Apple App Store. Explore Guides. Telegram Join. The complete guide to securing your privacy using two-factor authentication. |
| 2fa authentication bitcoin | Is bitcoin going to recover |
| 2fa authentication bitcoin | These tokens often have a long battery life of several years. If you require multiple device support, Authy is probably the best way to go. Choose strong and unique passwords for your accounts and avoid using the same password across different platforms. Email authentication is another common form of 2FA. Blockchain technology is changing the world. For the most part, things usually goes well, but when something bad happens, it becomes catastrophic. |
| 2fa authentication bitcoin | 345 |
| Crypto game simulator | African bitcoin lottery banks |
| 2fa authentication bitcoin | 265 |
| Tutorial minerando bitcoins to usd | Passwords have been a long-standing and ubiquitous form of authentication, but they have notable limitations. When logging into a Bitcoin wallet or trading platform with 2FA enabled, you would first enter your unique username and password as the initial level of verification. These apps provide an added layer of security by generating unique codes that are valid for only a short period of time. To use a software token, users must download the application on their computer or mobile device. In the event that your device is somehow lost, stolen, damaged, or just replaced, you have the means to recover your 2FA app on a new device. |
crypto mining calculator eth
?ME ESTAFARON! PERDI 1000 CON ARBITRAJE P2PTwo-factor authentication adds security by requiring two forms of authentication, like a password and a one-time code, for account. Two-factor authentication provides an extra layer of security to your crypto wallet by demanding two forms of. Click on your profile icon in the upper-right corner of the page. Select Settings and then Security. Scroll down to the 2FA table.
Share: